AWS CodePipeline¶
AWS provides two developer services for building code, AWS CodePipeline and AWS CodeBuild. The former being an orchestration tool, while the later executes each stage using a buildspec file. This guide assumes both were configured manually through the AWS Console and only focuses on the gotchas1.
CodePipeline¶
By default, CodePipeline clones a repository to S3 without the .git metadata folder. A full clone2 is needed for Uplift to run.
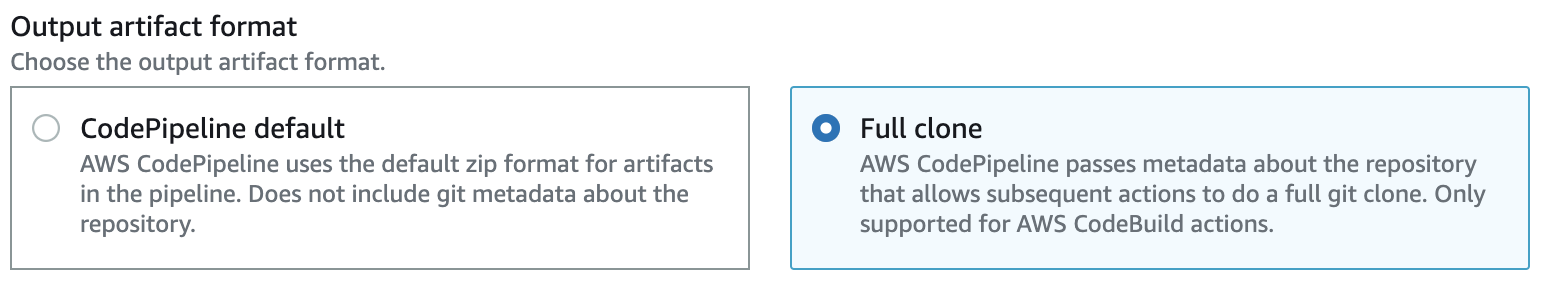
CodeBuild¶
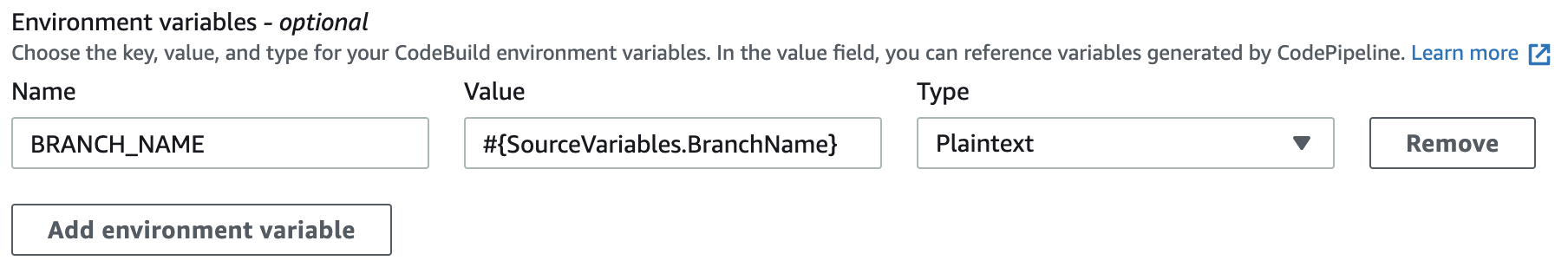
CodeBuild will always receive a git clone with a detached HEAD. By default, Uplift will error in this scenario. If performing a release, this will need to be resolved through a git checkout. However, the branch name is not exposed to CodeBuild by default. CodePipeline provides a variable #{SourceVariables.BranchName} that can be mapped to CodeBuild as an environment variable:
IAM¶
Additional permissions are needed to pull and push code within AWS CodeBuild. These vary based on the SCM used.
Principle of Least Privilege
For illustration purposes, a resource type of "*" is used. This should always be narrowed to the specific resource when possible.
CodeCommit¶
Both the codecommit:GitPull and codecommit:GitPush IAM permissions are needed and should be added to the CodeBuild service role.
GitHub¶
The codestar-connections:UseConnection IAM permission is needed when interacting with GitHub through an AWS CodeStar connection.
Buildspec¶
The buildspec will change depending on the CodeBuild project base image.
Default Amazon Images¶
Tested against the Amazon Linux 2, Ubuntu and Windows variants.
- Without this Uplift will lack any credentials when attempting to push code back to the source SCM.
- The
BRANCH_NAMEenvironment variable can be referenced directly within the buildspec, once mapped.
Official Uplift Image¶
Tested against the public gembaadvantage/uplift image.
Dealing with DockerHub Rate Limits
There are known issues with accessing public DockerHub repositories from AWS services, documented here.